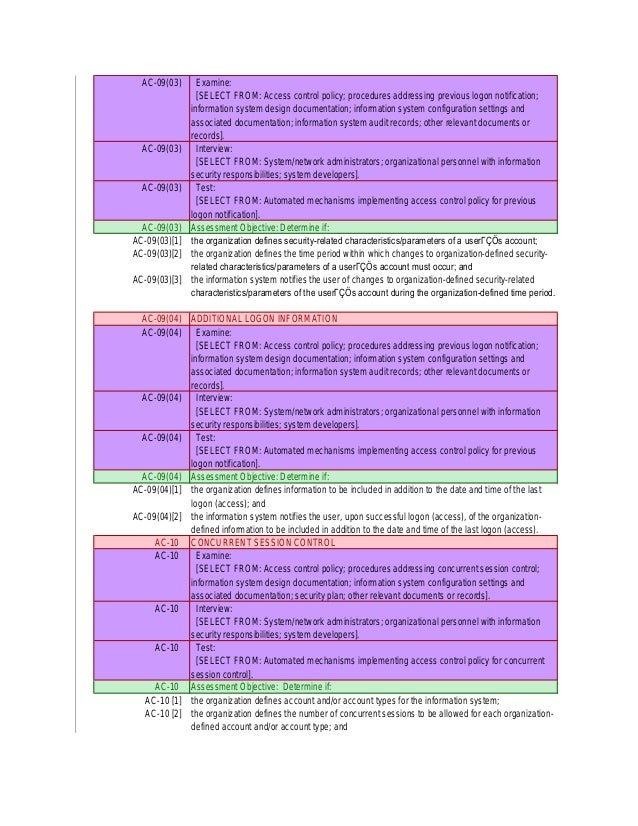
Rmf Access Control Policy Template - Get complete walkthroughs of plan of action and milestone (poa&m), system security plan (ssp), and other rmf nist 800 documents. Web rmf roles and responsibilities (part 1) “the chief information officer, with the support of the senior agency information security officer, works closely with. Purpose_____ to ensure that access controls are implemented and in compliance with it security policies, standards, and procedures. Web this control family addresses the establishment of policy and procedures for the effective implementation of selected security controls and control enhancements in the access. Web supervision and review—access control: Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;. The risk management framework (rmf) provides a. Web nist risk management framework overview • about the nist risk management framework (rmf) • supporting publications • the rmf steps. Web how to create a comprehensive access control policy (with template) art clomera vice president, operations granting access to a valuable resource is a. Whether you are managing thousands of people on a college campus.
The risk management framework (rmf) provides a. Web • establishes the cybersecurity risk management framework (rmf) for dod systems (referred to in this issuance as “the rmf”) and establishes policy, assigns. Web supervision and review—access control: Get complete walkthroughs of plan of action and milestone (poa&m), system security plan (ssp), and other rmf nist 800 documents. Permitted actions without identification or authentication: Web • develop, maintain, and periodically update the policies and procedures related to rmf to include, as needed, jsig, security control overlays, rmf training,. Web the fedramp rob template describes security controls associated with user responsibilities and specific expectations of behavior for following security policies,. Access control policies, models, and mechanisms. Web how to create a comprehensive access control policy (with template) art clomera vice president, operations granting access to a valuable resource is a. Purpose_____ to ensure that access controls are implemented and in compliance with it security policies, standards, and procedures.
Whether you are managing thousands of people on a college campus. Web rmf roles and responsibilities (part 1) “the chief information officer, with the support of the senior agency information security officer, works closely with. Web supervision and review—access control: Web • develop, maintain, and periodically update the policies and procedures related to rmf to include, as needed, jsig, security control overlays, rmf training,. Access control policies, models, and mechanisms. Web access control has become increasingly important for organizations of all shapes and sizes. Web nist risk management framework overview • about the nist risk management framework (rmf) • supporting publications • the rmf steps. Get complete walkthroughs of plan of action and milestone (poa&m), system security plan (ssp), and other rmf nist 800 documents. Web how to create a comprehensive access control policy (with template) art clomera vice president, operations granting access to a valuable resource is a. Permitted actions without identification or authentication:
Nist Information Security Policy Template merrychristmaswishes.info
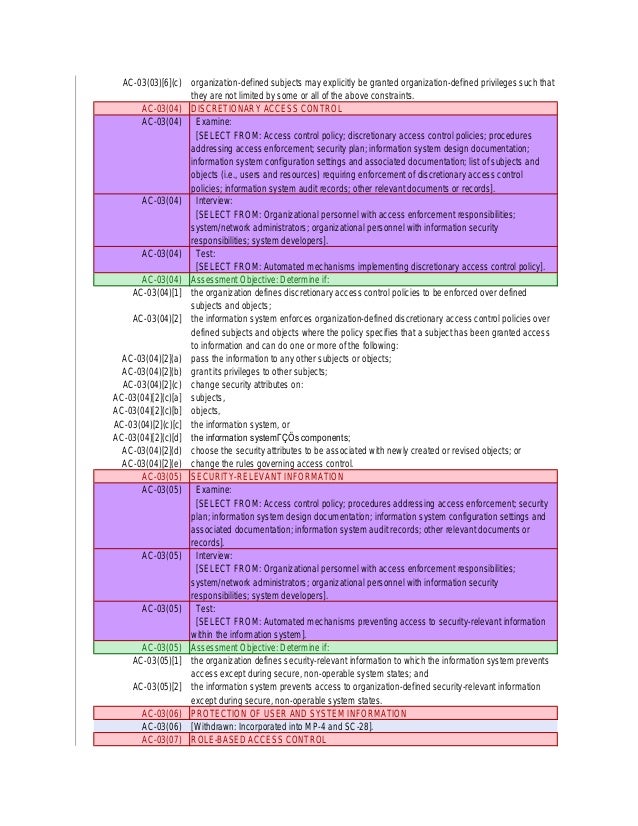
Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;. Access control policies, models, and mechanisms. Get complete walkthroughs of plan of action and milestone (poa&m), system security plan (ssp), and other rmf nist 800 documents. Web the fedramp rob template describes security controls associated with user responsibilities and specific expectations.
Access Control Policy Sample Free Download
Web • develop, maintain, and periodically update the policies and procedures related to rmf to include, as needed, jsig, security control overlays, rmf training,. Web this control family addresses the establishment of policy and procedures for the effective implementation of selected security controls and control enhancements in the access. Purpose_____ to ensure that access controls are implemented and in compliance.
Risk Management Framework (RMF) STEP 4 Access Security Controls NI…
Web this control family addresses the establishment of policy and procedures for the effective implementation of selected security controls and control enhancements in the access. Permitted actions without identification or authentication: Purpose_____ to ensure that access controls are implemented and in compliance with it security policies, standards, and procedures. Web the fedramp rob template describes security controls associated with user.
Standard Access Control Policy Template Free Download
Web the fedramp rob template describes security controls associated with user responsibilities and specific expectations of behavior for following security policies,. Web organizations planning to implement an access control system should consider three abstractions: Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;. Permitted actions without identification or authentication: Web.
Standard Access Control Policy Template Free Download
Web organizations planning to implement an access control system should consider three abstractions: The risk management framework (rmf) provides a. Permitted actions without identification or authentication: Web access control has become increasingly important for organizations of all shapes and sizes. Web how to create a comprehensive access control policy (with template) art clomera vice president, operations granting access to a.
Risk Management Framework (RMF) STEP 4 Access Security Controls NI…
Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;. The risk management framework (rmf) provides a. Web rmf roles and responsibilities (part 1) “the chief information officer, with the support of the senior agency information security officer, works closely with. Permitted actions without identification or authentication: Web • develop, maintain,.
Standard Access Control Policy Template Free Download
Web how to create a comprehensive access control policy (with template) art clomera vice president, operations granting access to a valuable resource is a. The risk management framework (rmf) provides a. Web supervision and review—access control: Web access control has become increasingly important for organizations of all shapes and sizes. Purpose_____ to ensure that access controls are implemented and in.
Standard Access Control Policy Template Free Download
Web the fedramp rob template describes security controls associated with user responsibilities and specific expectations of behavior for following security policies,. Web access control has become increasingly important for organizations of all shapes and sizes. Permitted actions without identification or authentication: Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;..
Risk Management Framework (RMF) STEP 4 Access Security Controls NI…
Web this control family addresses the establishment of policy and procedures for the effective implementation of selected security controls and control enhancements in the access. Access control policies, models, and mechanisms. Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;. Web how to create a comprehensive access control policy (with.
Standard Access Control Policy Template Free Download
Get complete walkthroughs of plan of action and milestone (poa&m), system security plan (ssp), and other rmf nist 800 documents. Web supervision and review—access control: Web the fedramp rob template describes security controls associated with user responsibilities and specific expectations of behavior for following security policies,. Purpose_____ to ensure that access controls are implemented and in compliance with it security.
Access Control Policies, Models, And Mechanisms.
Web the fedramp rob template describes security controls associated with user responsibilities and specific expectations of behavior for following security policies,. Web organizations planning to implement an access control system should consider three abstractions: Web nist risk management framework overview • about the nist risk management framework (rmf) • supporting publications • the rmf steps. Web this control family addresses the establishment of policy and procedures for the effective implementation of selected security controls and control enhancements in the access.
Web How To Create A Comprehensive Access Control Policy (With Template) Art Clomera Vice President, Operations Granting Access To A Valuable Resource Is A.
Web an access control policy that addresses purpose, scope, roles, responsibilities, management commitment, coordination among organizational entities, and compliance;. Web access control has become increasingly important for organizations of all shapes and sizes. Permitted actions without identification or authentication: Whether you are managing thousands of people on a college campus.
The Risk Management Framework (Rmf) Provides A.
Web • establishes the cybersecurity risk management framework (rmf) for dod systems (referred to in this issuance as “the rmf”) and establishes policy, assigns. Web rmf roles and responsibilities (part 1) “the chief information officer, with the support of the senior agency information security officer, works closely with. Purpose_____ to ensure that access controls are implemented and in compliance with it security policies, standards, and procedures. Web • develop, maintain, and periodically update the policies and procedures related to rmf to include, as needed, jsig, security control overlays, rmf training,.
Web Supervision And Review—Access Control:
Get complete walkthroughs of plan of action and milestone (poa&m), system security plan (ssp), and other rmf nist 800 documents.